The rapidly advancing digital space has brought cloud computing as a necessity for the business world today. Cloud hosting allows companies to store, manage, and access data from anywhere over the internet rather than a local server. However, with more reliance on such technology, it is becoming a critical necessity for guarding sensitive information that cannot be accessed with cyber threats.
In this regard, cloud security is that subcategory of cybersecurity which specifically deals with protecting the cloud computing environment and various strategies, technologies, and policies designed to safeguard the data, applications, and infrastructure of a cloud network. In light of more organizations migrating their operations to cloud computing, it becomes essential to know how to implement cloud computing security to minimize the possible risks emerging from possible breaches of data, malware attacks, or the unintended loss of data.
In this blog, we’ll uncover what cloud security means, specifically developed risks in cloud hosting, and the strategies to effectively secure resources-based in the cloud. We’ve also included information on the risks of cloud security and whether cloud hosting is secure as more and more companies rely on cloud hosting providers to take care of their IT requirements. With this article, you’ll be better equipped to know at the end of it all just how you can design a strong cloud security strategy and figure out how you can find the best cloud hosting provider for your organization’s needs.
Understanding Cloud Security
One of the cybersecurity facets specifically designed to protect cloud computing environments is cloud security. With more and more data, applications, and resources hosted in the cloud, that means more and more people need to take careful steps to protect their cloud assets from growing cyber threats. It becomes a very different kind of data security compared to a traditional data environment, which resides on-premises within company networks. Such a change in location demands a new approach to protecting information, very specific and, therefore, requiring special sets of tools and strategies.
At its core, cloud security relates to the protection of unauthorized access, data breaches, and everything else malicious by ensuring appropriate policies and technologies for cloud-based systems. Cloud computing security encompasses every measure from access measures and data encryption to network configurations that forestall external threats. More often than not, companies will team with the cloud hosting provider they have settled on to understand specific security mechanisms available and ensure proper setup.
Since cloud security has derived its uniqueness from traditional IT security, the uniqueness of cloud computing in respect to business vulnerabilities becomes very important.
In comparison to traditional IT setups, cloud hosting is different because, with third-party providers offering server management services, firms do not handle both hardware and infrastructure themselves. But the requirement for transparency in security policy by dependence on external cloud providers arises because organizations must place data in the possession of these providers, so their security measures will depend on not leaking data, and other similar threats.
Types of Cloud Security
Data Security is one of the building blocks of cloud security: it involves the safe storage, transfer, or processing of data in any cloud environment. Often this is implemented through encryption, whether the data is stored or in transit, so that an unauthorized party cannot access sensitive information. Other important strategies are data loss prevention strategies, as they create backup copies of the data and make use of redundancy tactics to prevent losses from accidental or malicious breaches. To ensure secure data at all levels, there should be no leak or breach of data, and it must be kept confidential and of integrity in the cloud.
Network security in the cloud is concerned with protecting the routes that data travel through. It includes firewalls, VPNs, and IDS blocking unauthorized access as well as malicious traffic. Network segmentation means dividing a cloud environment into separate isolated parts-to minimize the possible damage spread within that network. Distributed over the internet through cloud providers, data therefore renders a necessity for implementing network security measures to protect against threats targeting network vulnerabilities.
Application Security is very fundamental as applications that are cloud-hosted have many portals of access, from which they stand vulnerable to SQL injection, cross-site scripting amongst other web-based threats. The interface of the application security involves safe coding practices and continuous security testing and management of vulnerabilities in the structural make-up of the application. The extension of cloud security to the level of the application ensures that there is an all-rounded way of protecting data and processes against exploit events.
Cloud Security Risks
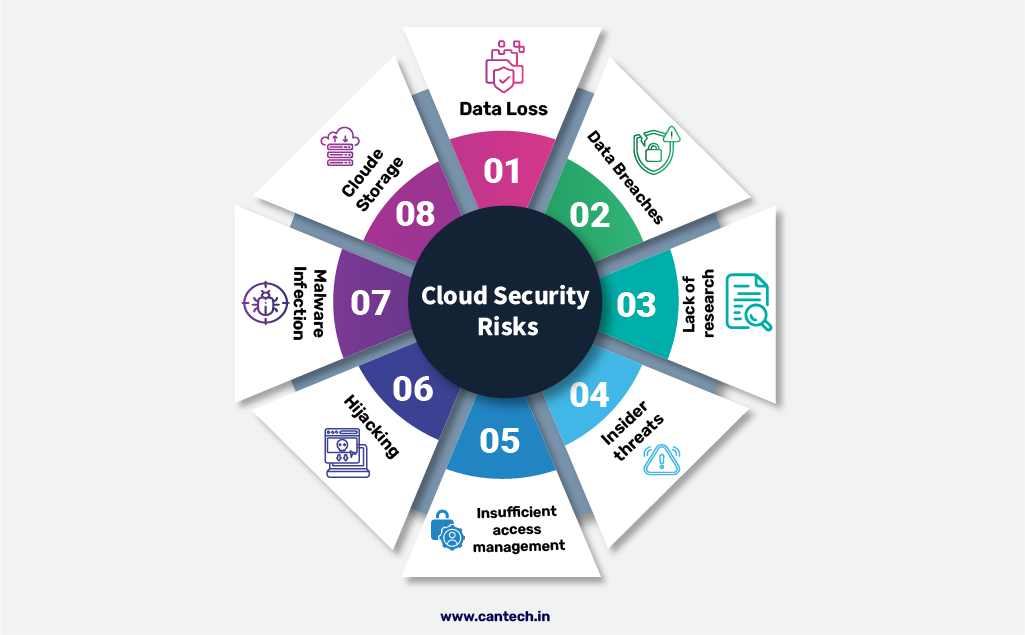
Data breaches are one of the biggest threats of cloud computing. In the case of a breach in the cloud, customer data, sensitive information, such as important copyrights, financial records, etc., can be unlocked. Until now, attack vulnerabilities may easily be exploited if the security measures of the cloud are weak thus allowing unauthorised access to the valuables. These data breaches may result in heavy losses financially or reputational damages or even become a cause for legal action, especially when customer data is breached. Based on the criteria mentioned, security against breaches of data is highly valued in the context of cloud computing.
Another important cloud security threat is account hijacking. It involves unauthorized access to a user’s account, sometimes by phishing or using very weak passwords. Once an account falls into the hands of attackers, they can manipulate data, change access controls, and also misappropriate resources, all without knowing and forewarning the account owner. In this regard, strong authentication methods, such as multi-factor authentication, provide an additional layer of security for cloud users.
Loss and leakage of data in the cloud hosting environment pose a significant threat because companies may lose confidential data unintentionally due to accidental action or even intentional instances due to human ignorance or system failure/malicious intent. The other risk associated with cloud is related to regulatory and compliance, as laws relating to protection of data vary from place to place. These risks combined with close cooperation with cloud hosting providers regarding compliance with both regional and industry standards to avoid costly fines with the client trust intact is a major concern for businesses dealing with confidential information.
Cloud Security Best Practices
This is an important first step in cloud security, as this will allow companies to apply the right amount of protection to the right kind of data. Sensitive data, such as financial or personal information, may need much more robust encryption and access controls than less critical data. This will help organizations concentrate their resources on the valuable cloud information that needs better protection.
Among all elements, access control and identity management are considered key elements in the securing of cloud environments since they define who accesses any given data and resources. Strict access control policies help minimize the risk of unauthorized access in companies. The hallmark of identity management systems lies in handling user identities and permissions for controlling access to cloud resources. Multi-factor authentication is frequently utilized in an organization for additional security against unauthorized access to sensitive data.
There are quarterly audits and compliance checks to ensure security and strict adherence to the regulations. This includes cloud security protocols; whether they are at the benchmark standard required by the industry, or if they exist somewhere that’s vulnerable or outdated. Compliance to data protection, for example, such as GDPR or HIPAA is critical for companies operating in regulated industries. If they fail to adhere to these regulatory standards, it can lead to massive financial penalties and legal repercussions. Keeping cloud security practices up to date is very important because of the rapidly changing nature of threats.
Role of Cloud Hosting Providers in Cloud Security
The cloud security model under the shared responsibility is considered to be one of the most central aspects of it. It specifies how the providers and consumers share their responsibility toward securing the cloud environment. Providers in general will take care of physical infrastructures as well as the core of all the services offered through them, whereas the customers shall ensure that the data, the applications, and user access related to them are secured in their cloud environment. This helps companies understand their responsibilities, which in turn enables them to focus on securing the parts they have control over.
Cloud service providers may entail offering customer’s data encryption, firewalls, and intrusion detection tools to be used in addition to enhancing security features. Cloud hosting sites offer complex threat detection and identity management services, through which the organization can trace access activities to their data. In choosing a cloud hosting provider, an organization should consider the types of security services being offered and compare those to their specific security requirements.
Cloud security provider evaluation is very important for businesses to ensure that their cloud environment is safe. Such key considerations revolve around the practices of data encryption, incident response capabilities, and compliance with industry standards. Providers that have a good reputation for security, which may be supported by ISO 27001 certification, ensure the standards are maintained at the high levels of cloud security and the safety of customer data from many forms of threats.
Creating a Cloud Security Strategy
The first step in creating a robust cloud security strategy is to understand specifically what the individual security needs are for an organization and what regulatory requirements apply. Different organizations have different kinds of security needs, as some depend on what kind of data the organization holds and what kind of regulatory obligations it may have. It helps them understand where they might be vulnerable and identifies areas where some extra security might be required.
The security policy must produce the policies that govern, manage, and monitor cloud resources. Access control, data protection, and incident response are just some of the components that a well-crafted security policy pays attention to. It is a guide or framework on how best to approach a cloud environment’s safety: every employee is cognizant of his or her responsibilities in ensuring that the cloud remains safe. It is policy-based, which means there is coordination and responsibility within the entity.
Training and awareness programs help the employees stay aware of the best practices for cloud security and the latest threats. Continuous education and awareness campaigns help an employee understand the protocols for cloud security and how they must respond to potential threats at any given point of time. Security is a shared responsibility within an organization, and a well-trained workforce can be the first line of defense against security incidents.
Is Cloud Hosting Secure? The Future of Cloud Security
It is quite important to note that while a cloud provider extends maximum effort in security matters, the customer too needs to take its share to secure its information. Majority of providers offer advanced security functionalities; however, businesses have to put proper controls over access, encryption, and other mechanisms to complement such features. Cloud hosting can always be made secure if both the provider and customer proactively act upon providing complete security measures. Using the cloud shared responsibility model, it highlights that security in the cloud is most effectively produced when there is collaboration and sharing in securing the environment. Having an understanding of their varied security needs, companies can enter cloud hosting with greater confidence in an effort to reduce risks.
Cloud security is constantly evolving through new technologies. Artificial intelligence and machine learning are being introduced into systems to detect threats in real-time, analyze unusual patterns, and respond to security incidents automatically. Advanced technologies are thus being used to provide predictive analytics for the detection of vulnerabilities before they become critical issues. With growing complexity in cyber attacks, one can envision AI-driven security tools to become much more the norm in the existing and future cloud computing security measures.
Looking ahead, the future of cloud security will continue evolving to address new challenges and leverage emerging trends. With cloud adoption expanding, organizations will increasingly rely on multi-cloud and hybrid cloud environments, requiring new strategies for managing security across different platforms. The future of cloud security will also involve greater automation, improved incident response mechanisms, and the integration of zero-trust principles, where no entity is trusted by default, making cloud environments even more resilient to evolving threats.
Conclusion
Cloud security is quite important for any organization that is using cloud computing to gain power over technology. Evolving threats range from data breaches to malware and unauthorized accesses. Businesses need a proactive approach to securing their cloud environments against all such threats. Understanding cloud security risks and choosing a reliable cloud-hosting provider ensures that an organization can fully exploit the potential of cloud computing while minimizing vulnerabilities.
Therefore, the strategy of the cloud should be robust, with access controls, encryption, regular audits, and educating employees on best practices. The implementation of cloud security measures will improve and advance with technology, protecting digital assets for businesses and customers. Organisations can make sure that these are high-security clouds by having careful planning and a commitment to continuous improvement.
Besides knowing the best practices for use in cloud security, an efficient provider is needed in creating a secure environment. The Cantech Cloud Hosting Servers are crafted with the highest quality and security to ensure that the data will be kept intact, safe, and available to every type of business. Advanced measures of powerful network security and multi-factor authentication even the most complex encryption is involved in shielding the business against all malicious access and cyber-attacks in Cantech’s advanced cloud hosting solutions.
With scalable infrastructure and 24/7 monitoring, Cantech prioritizes performance and security, thus making it a go-to choice in cloud computing for businesses that will exploit the benefits with confidence. Since Cantech can support the companies’ secure, resilient environment in the cloud and help them boost growth and innovation, it is a much welcomed solution.
FAQs
What is cloud security, and why is it important?
Cloud security refers to the general practices, strategies, and technologies implemented to protect cloud computing environments against data breach and cyber-attack and other forms of security threats. As firms become more reliant on the cloud solutions for storing their data and running applications, cloud security becomes a new imperative for any firm eager to protect sensitive information and adherence to data protection regulations. What a proper framework in the cloud does is deter unauthorized access to or any misplaced data-the very essence of business-continuity support. The cloud would then be one of the viable options for playing around with computing flexibility and scalability without trading off on safety.
What are the main types of cloud security threats?
Cloud environments face myriad security threats ranging from data breaches and account hijacking to denial-of-service attacks as well as insider threats. The highest risk is data breaches since any form of sensitive information stored on the cloud may fall into wrong hands if left unsecured. Account hijacking allows attackers to gain control over the user accounts available on the cloud, hence gaining unauthorized access to such critical systems and data. Distributed Denial-of-service attacks pose a threat that may overwhelm the resources of the cloud and cause service disruption and impact business operations.
What role do cloud providers play in cloud security?
One of the things cloud providers should provide includes physical security measures, securing data centers, and networking defenses against outside threats. Most cloud providers also offer different kinds of security features like data encryption, firewalls, and identity and access management tools for businesses to use and supplement their cloud security. In the shared responsibility model, however, customer responsibilities such as securing applications, managing user access, and industry standards compliance are on the customers’ side.
Can small businesses benefit from cloud security measures?
Small businesses can greatly benefit from cloud security measures as they often lack the resources for extensive on-premises security infrastructure. By using cloud services with built-in security features, such as encryption and threat detection, small businesses gain access to high-level security typically available to larger companies. Cloud providers also help small businesses meet compliance requirements without investing heavily in IT resources. As a result, small businesses can securely leverage cloud technology to streamline operations, reduce costs, and focus on growth, knowing their data and applications are protected.
What are some best practices for enhancing cloud security?
To improve cloud security, businesses should follow best practices such as implementing multi-factor authentication, encrypting data at rest and in transit, and using strong access controls. Regularly updating software and applying security patches can also prevent vulnerabilities from being exploited by cybercriminals. Organizations should conduct security assessments, establish policies for data classification and access management, and provide security training for employees. Furthermore, monitoring and logging activities within the cloud environment are essential for detecting potential threats in real-time. Following these practices helps minimize security risks and ensures a more secure cloud infrastructure.